Deploying AKO via Helm on vSphere with Tanzu on NSX-T
AKO
via Helm on vSphere with Tanzu on NSX-TThe
Avi Kubernetes Operator
(AKO
) is an operator which works as an ingress Controller and performs functions specific to Avi Load Balancer
in the TKGs environment with the Avi Load Balancer Controller
. It remains in sync with the necessary TKGs objects and calls Controller APIs to configure the virtual services.The
AKO
deployment consists of the following components:- TheAvi Load Balancer Controller
- The Service Engines (SE)
- TheAvi Kubernetes Operator(AKO)
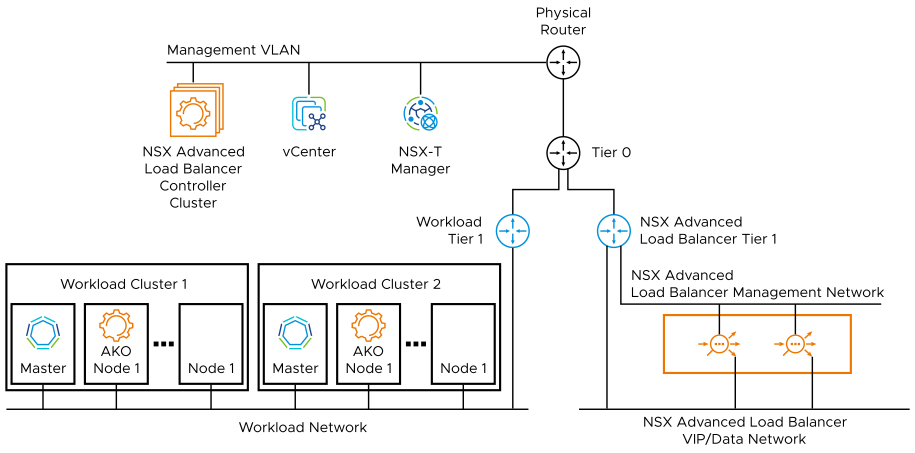
An overview of the
AKO
deployment is shown below:
Security restrictions prevent
AKO
from communicating with an Avi Load Balancer Controller
installed in the management domain where VCenter or NSX-Manager is located. The Avi Load Balancer Controller
can be deployed anywhere, assuming AKO
can route to it.Deployment Guide
AKO
can be installed on each workload cluster, using HELM to sync only ingress. Load Balancer sync must be deactivated on AKO
because NSX-T LB cannot be turned off, and AKO
and NCP will overwrite the LB VIP if both are managing the LB service.Create Two Tier-1s for Avi Load Balancer
Avi Load Balancer
In NSX-T Manager, create a new dedicated Tier-1 Gateway for use with
Avi Load Balancer
Management. Also, create an additional Tier-1 Gateway for use as the Avi Load Balancer
VIP Network. This will allow north-bound connections to T0 gateways and south-bound to the individual segments.
The architecture of the
T1-Avi-Mgmt
is shown above.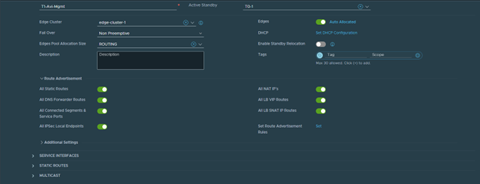
Ensure that the proper route advertisements are configured so that
Avi Load Balancer
can redistribute the VIP routes to the T0 gateway.For detailed instructions on how to create this T1, see .
Installing NSX Advanced Load Balancer in VMware NSX-T Environments
topic in the VMware Avi Load Balancer
Installation GuideCreate a Segment under each Avi Load Balancer Tier-1
Avi Load Balancer
Tier-1The
Avi Load Balancer
requires a segment to be created under each of the Tier 1, one segment for Management and the other for Vip/Data.
For additional details, see .
Installing NSX Advanced Load Balancer in VMware NSX-T Environments
topic in the VMware Avi Load Balancer
Installation GuideConfigure NSX-T Cloud on Avi Load Balancer
Avi Load Balancer
The point of integration in .
Avi Load Balancer
, with any infrastructure, is called a cloud. For the NSX-T environment, an NSX-T cloud has to be configured. For more information on configuring an NSX-T cloud, see Installing NSX Advanced Load Balancer in VMware NSX-T Environments
topic in the VMware Avi Load Balancer
Installation GuideSet Default Gateway in Avi Load Balancer
Avi Load Balancer
Set Default Gateway for the T1 vrf in
Avi Load Balancer
. The DG needs to be set to allow outbound traffic from the Avi Load Balancer
VIP/Data segment and the Management segment. See the following screenshot for an example. First, the Data/Vip DG is set in VMware Avi Load Balancer
, as shown below:
Next, the Management DG needs to be set, if DHCP is not available. This is done using CLI.
Example commands:
shell switchto cloud nsxt terminal mode linux_command_line configure vrfcontext management --static_routes.1.prefix 0.0.0.0/0 --static_routes.1.next_hop 172.16.30.1 --static_routes.1.route_id 1
Configure VMware Avi Load Balancer IPAM Profile
VMware Avi Load Balancer
IPAM ProfileThe
VMware Avi Load Balancer
allocates IP addresses from a pool of IP addresses within the subnet configured as shown below. After creating this profile, Modify the NSX-T cloud and add this profile.
For more information, see .
Configuring
topic in the Avi Load Balancer
IPAMVMware Avi Load Balancer
Installation GuideConfigure VMware Avi Load Balancer DNS Profile
VMware Avi Load Balancer
DNS ProfileAKO
needs to be authoritative in the domain that is specified below. After creating the profile, Modify the NSX-T cloud and add the profile.
For more details, see .
Avi Load Balancer
IPAM and DNS topic in the VMware Avi Load Balancer
Installation GuideConfigure NSX-T DFW Rules
The default rule in WCP will deny all ingress traffic. Configure a DFW rule to allow SEs to the backend nodes/pods. Configure additional DFW rules to allow clients to VIPs and E-W SE-SE Traffic.

Deploy AKO through Helm
AKO
through HelmConfigure the appropriate fields in the
values.yaml
file to allow AKO
to integrate with VMware Avi Load Balancer
+ NSX-T.- layer7Only– Set toTrue
- L7Settings.serviceType– UnderL7Settings, set toNodePort
- nsxtT1LR– Full path to theVMware Avi Load BalancerTier 1. Example: “/infra/tier-1s/Avi-T1”
- vipNetworkList– Set to theVMware Avi Load BalancerVIP Network
- ControllerSettings– Set these forVMware Avi Load Balancerand the NSXT Cloud
- avicredentials– Optional, can be passed through CLI
The full path for
VMware Avi Load Balancer
Tier1 in NSX-T can be found through an VMware Avi Load Balancer
CLI command:
Installing AKO
AKO
helm install ako/ako --generate-name --version 1.7.1 -f /ako/values.yaml --set avicredentials.username=admin --set avicredentials.password='password123' --namespace=avi-system
The above command will create a pod named:
ako-0
in the avi-system
namespace. Nothing will be created in VMware Avi Load Balancer
until an ingress is created.For detailed instructions on how to deploy
AKO
through helm, see Install Avi Kubernetes Operator.